Unlocking IT Quality: Your Regional Managed Provider
Unlocking IT Quality: Your Regional Managed Provider
Blog Article
Strategize and Range WITh Proven IT Managed Services Methods
In the hectic landscape of modern-day business, the strategic usage of IT managed services has actually become a cornerstone for companies intending to enhance functional efficiency and drive lasting growth. By applying proven techniques customized to satisfy certain organization needs, companies can browse the intricacies of innovation while continuing to be affordable and agile in their corresponding industries.
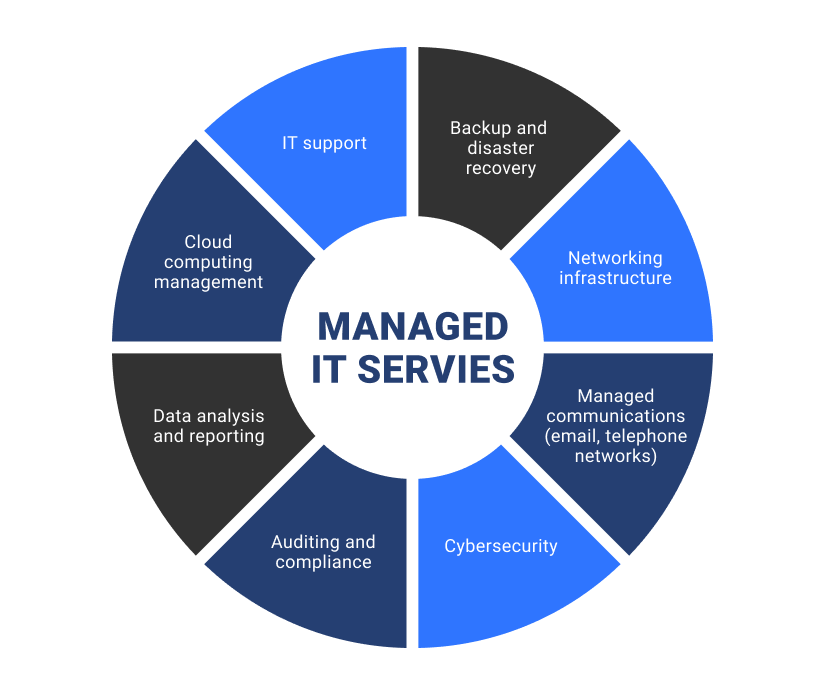
Benefits of IT Handled Services
Undoubtedly, the benefits of IT Managed Solutions are extremely important in improving organizational efficiency and reducing downtime. By outsourcing IT administration to a specialized supplier, organizations can touch right into a wide range of proficiency and resources that would otherwise be costly to keep internal. Among the crucial benefits of IT Handled Services is positive monitoring and maintenance of systems, which helps protect against possible concerns prior to they intensify into significant troubles. This positive method translates into better system uptime, minimized downtime, and improved overall productivity for the company.
Moreover, IT Managed Provider can supply access to the most recent innovations and ideal methods without the demand for continuous investment in training and facilities upgrades. This ensures that services stay competitive in a quickly evolving technical landscape. Additionally, by offloading regular IT tasks to a taken care of providers, internal IT teams can concentrate on tactical campaigns that drive innovation and growth for the company. In conclusion, the benefits of IT Managed Providers contribute in enhancing procedures, increasing effectiveness, and inevitably, driving company success.
Secret Methods for Execution
With an understanding of the considerable advantages that IT Managed Provider deal, companies can now concentrate on carrying out essential strategies to efficiently integrate these services right into their operations - it managed service providers. Additionally, organizations need to establish clear interaction channels with their managed solution company to ensure smooth partnership and prompt problem resolution.
Another critical method is to prioritize cybersecurity procedures. Data violations and cyber risks posture considerable threats to services, making safety and security a leading priority. Carrying out robust safety protocols, routine monitoring, and prompt updates are essential actions in safeguarding sensitive details and preserving organization continuity.
Moreover, businesses must develop service degree arrangements (SLAs) with their managed provider to define assumptions, responsibilities, and performance metrics. SLAs assist in establishing clear guidelines, making sure liability, and preserving solution quality criteria. By incorporating these crucial strategies, services can leverage IT Handled Provider to streamline operations, improve performance, and drive lasting growth.
Maximizing Effectiveness Via Automation
Furthermore, automation allows real-time tracking and data evaluation, giving beneficial understandings for educated decision-making. By automating routine monitoring jobs, organizations can proactively attend to problems before they rise, decreasing downtime and enhancing performance (managed service provider). Additionally, automation can facilitate the smooth combination of various systems and applications, improving collaboration and data circulation across the company
Ensuring Information Safety And Security and Conformity
Data safety and compliance are vital problems for businesses running in the digital landscape these days. With the raising quantity of sensitive data being saved and processed, ensuring robust safety steps is crucial to guard versus cyber threats and follow regulatory her latest blog demands. Applying extensive more helpful hints data safety and security practices includes encrypting information, developing access controls, routinely updating software application, and conducting safety audits. Complying with regulations such as GDPR, HIPAA, or PCI DSS is vital to preserve and avoid costly penalties trust with customers. Managed IT companies play an important function in helping businesses navigate the facility landscape of information protection and conformity. They use competence in carrying out safety protocols, keeping an eye on systems for possible violations, and making certain adherence to industry regulations. By partnering with a respectable managed companies, companies can improve their information safety stance, alleviate risks, and show a dedication to safeguarding the confidentiality and honesty of their data properties.
Scaling IT Facilities for Growth
Integrating scalable IT framework solutions is vital for facilitating company development and functional efficiency. As companies broaden, their IT requires advance, requiring facilities that can adjust to raised needs seamlessly. By scaling IT facilities successfully, companies can ensure that their systems remain reputable, safe, and performant also as work expand.
One secret element of scaling IT framework for development is the capacity to flexibly allocate resources based on current requirements. Cloud computing services, as an example, offer scalability by allowing companies to change storage, processing power, and other resources as needed. This elasticity enables firms to efficiently take care of spikes sought after without over-provisioning sources throughout durations of lower activity.
Furthermore, executing virtualization innovations can enhance scalability by enabling the creation of digital circumstances that can be quickly duplicated or modified to accommodate changing work - managed service provider. By virtualizing servers, storage, and networks, companies can enhance resource utilization and streamline IT monitoring procedures, eventually supporting organization development initiatives effectively
Verdict
Finally, executing IT managed solutions can bring numerous advantages to a company, such as enhanced performance, enhanced information security, and scalability for development. By complying with vital methods for implementation, making use of automation to maximize effectiveness, and guaranteeing information safety and security and conformity, services can better plan and scale their IT infrastructure. It is critical for organizations to advance and adapt with technical developments to remain competitive in today's ever-changing landscape.

Report this page